Linkedin 6.5m Password Leak Might be Tip of Iceberg
When I swung by Linkedin yesterday afternoon to be greated by my Linkedin Today headlines (CNET, Mashable, CBS News) showing that 6.5m Linkedin passwords were now in the public domain. Having spent a good deal of time at Chinwag's Careers Day explaining why building connections, maintaining a profile and asking for recommendations, it provides a salutory reminder that it's not just credit card and bank details that are vulnerable.
How would you fare if you're Linkedin connections disappeared? (If you're panicing enough not to read the rest of the post - here's Linkedin's advice on changing passwords) I bet there's a few recruiters out there who will blanch at the thought. The file of stolen passwords was posted on a popular hacking forum with a request for help in cracking them, which according to data security firm, Imperva, indicates this might just be the tip of the iceberg.
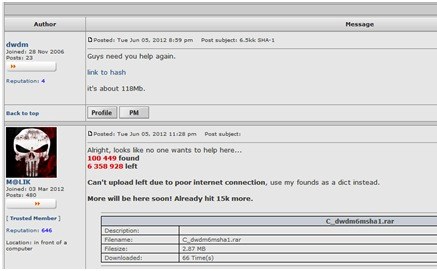
What gives the game away, says Imperva, are two key indicators:
- The password list is missing “easy” passwords - the files do not contain easy to crack passwords such as “123456” that are traditionally the most common choice of passwords. Most likely, the hacker has figured out the easy passwords and needs help with less common ones, so the hacker only published the more complicated ones.
- Passwords are typically listed only once - in other words, the list doesn’t reveal how many times a password was used by the consumers. A single entry in this list can be used by more than one person. For reference, in the RockYou hack the 5,000 most popular passwords, were used by a share of 20% of the users. We believe that to be the case here as well, another indicator that the breach size exceeds 6.5M.
One of the crucial elements missed in encrypting the passwords using a salt. Like a recipe where salt enhances the flavour, a salt does the same in cryptography, enhancing the security and making passwords substantially harder to guess.
Linkedin have blogged about the breach and advice to users on changing their passwords in the somewhat ironically titled blog post, "Updating Your Password on LinkedIn and Other Account Security Best Practices".
Update: Password management firm LastPass have released a tool to see if you're password was among the 6.5m stolen from Linkedin. Click here for: LastPass Linkedin tool.



Comments
And now it's Last.fm losing passwords...
Wow, bad times for IT Security professionals. Last.fm have just posted on their site about an incident where they believe some users' passwords may have been hacked.
They're also posted instructions on how to change your Last.fm password.